In December 2019 I published a whitepaper on Palo Alto Networks’ migration from Global Protect to Prisma Access for remote users. A few months later, COVID-19 happened. All of a sudden employees had to work at home or remotely, and securing remote access became a top priority for organizations.
Today, home networks are the new corporate networks. The corporate office has extended to the employee’s home, which contains work laptops, personal unprotected devices (e.g., kids gaming consoles), home IoTs, and who knows what else …. all on the same network with employee laptops and mobile devices connected to critical corporate resources.
Companies must address an expanded attack surface. Network security and SOC teams are in a dilemma in terms of how to best balance productivity with security. Key questions include how to provide security for remote users, company infrastructure, applications and intellectual property.
For Palo Alto Networks, we addressed secure connectivity with Prisma Access. But given that remote work is going to be the norm in a post-COVID world, we want to further harden security for intellectual property.
Our current infrastructure footprint worldwide is as follows:
- 35+ global sites: Composed of corporate sites, data centers, GCP cloud and partner sites.
- Firewalls: 200+ (60% physical and 40% VM-series), SD-WAN: ~50 CloudGenix devices for site-to-site connectivity.
- Prisma Access deployment: 10k+ mobile users, 10+ Service Connections, 10+ Remote Network sites, 100+ Prisma Access cloud gateways and 9+ Prisma Access on-prem hybrid gateways.
Additionally, for our end user security posture, we use always-on enabled for GlobalProtect Agents, adaptive MFA for all our SaaS and internal applications, machine/user based certificates on all laptops, mobile phones and XDR Agent on all laptops and servers.
Tightening Security
In order to tighten security to protect our intellectual property (code repositories, critical applications) and employee laptops remotely, we took measures to ensure that we know who is connecting to which corporate resources and with a minimum hardened security posture, as summarized below:
- Hardened endpoint posture through HIP (Host Information Profile) checks: We mandated access to internal corporate resources only through Palo Alto Networks issued laptops which pass the following HIP checks.
- Laptop has an anti-malware agent (e.g., XDR Agent) installed and is running in real-time protection mode
- Laptop has disk encryption enabled.
- Limit contractor access to only applications needed for relevant roles. Certificate, identity, MFA requirements still hold.
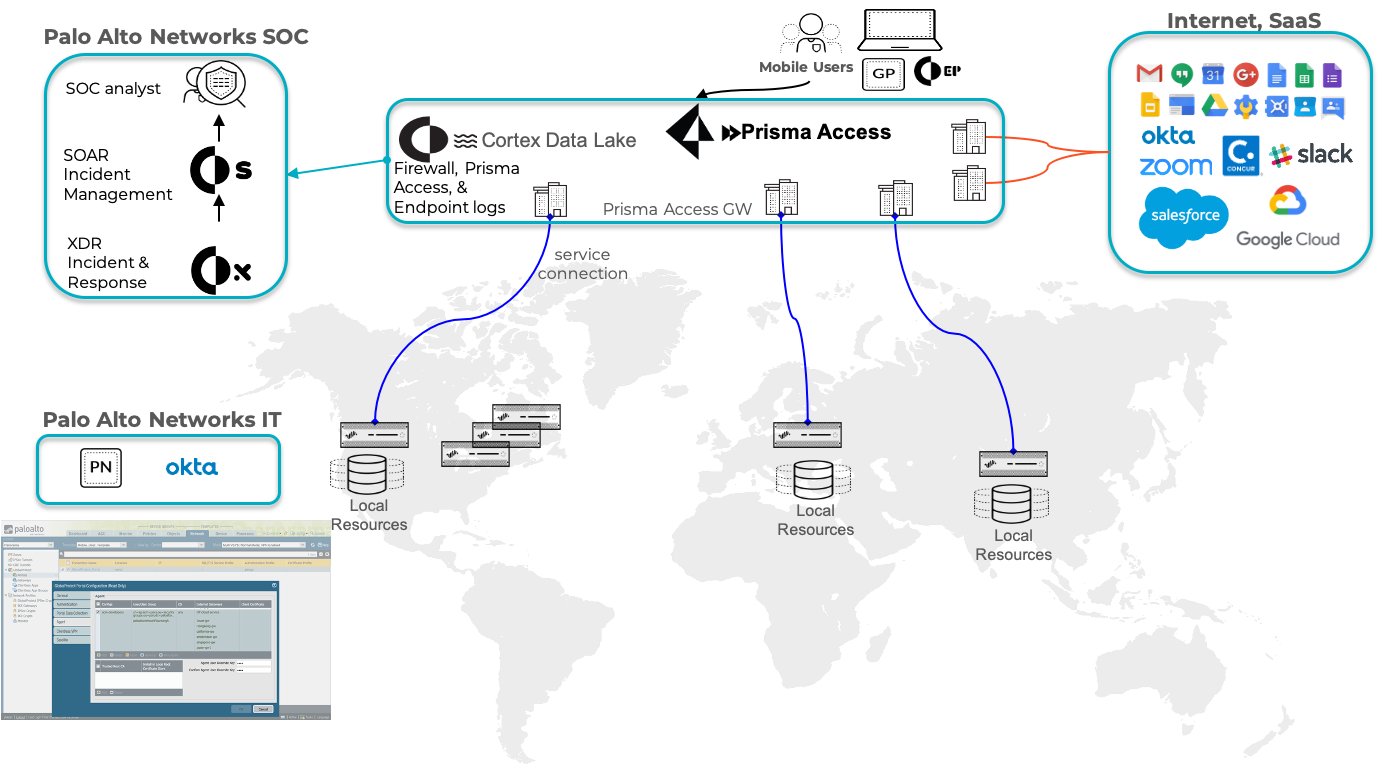
- End-point XDR Agent has BIOCs to protect registries and processes on laptops. If XDR Agent sees anything anomalous, XDR application will trigger a security alert in the SOC for a SOC analyst to review. The overall process is shown in figure 1 below.
- Limit corporate resources access only through Prisma Access gateways. This way we have visibility and controls of who’s accessing corporate resources.
- Identity management: We’re limiting developers to only use accounts associated with their corporate identity. This allows us to monitor/tighten end users who access accounts using unassociated corporate identities.
- Ensure full traffic visibility: All traffic goes through Prisma Access gateways and corporate firewalls by using GP Agent. This allows processing of all traffic using security rules and profiles that tie with Cloud Delivered Security Services (CDSS), such as Advanced URL filtering, DNS Security, IoT Security, Wildfire, etc.
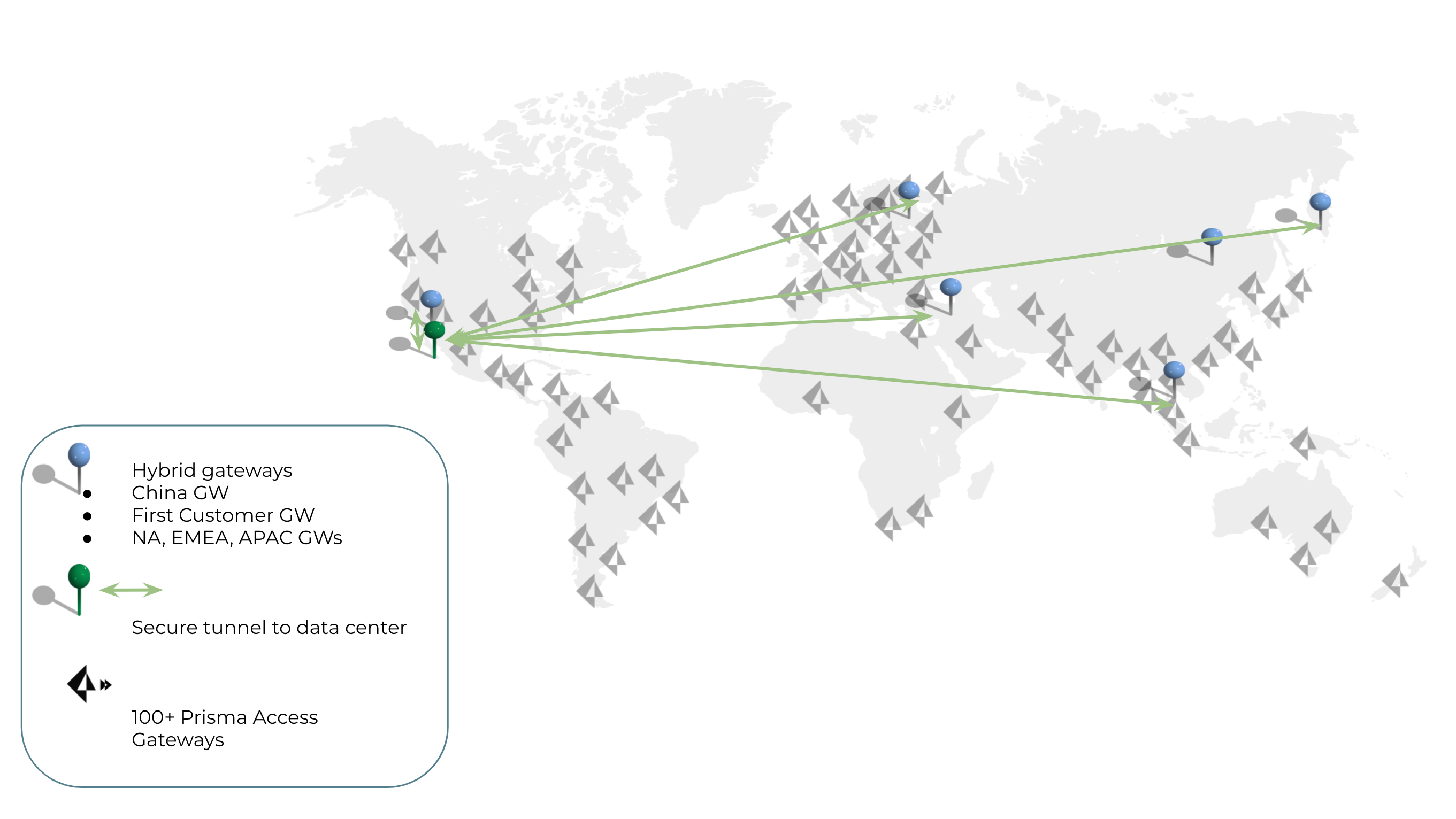
Hybrid Prisma Access Gateways
We added existing GP hybrid gateways (existing and new on-prem firewalls at various sites) under our Prisma Access portal to support specific business requirements related to performance and user experience improvements for remote IT, sales and engineering teams. These hybrid gateways are shown in figure 2 and address the following needs:
- Mainland China GP gateway to improve mainland China user experience connecting to corporate, SaaS applications and Google Cloud.
- First Customer GP gateway to use latest beta software and features with a few hundred users. Consider this a staging part of the network where we can rollout and track new capabilities before a full production rollout.
- Regional GP gateways in North America, Europe and Asia to provide developers low-latency access to local applications and labs.
- Secure connections from hybrid gateways to data centers to enable IT help desk workers to provide imaging support remotely from their homes in North America (NA), Europe (EMEA) and Asia (APAC).
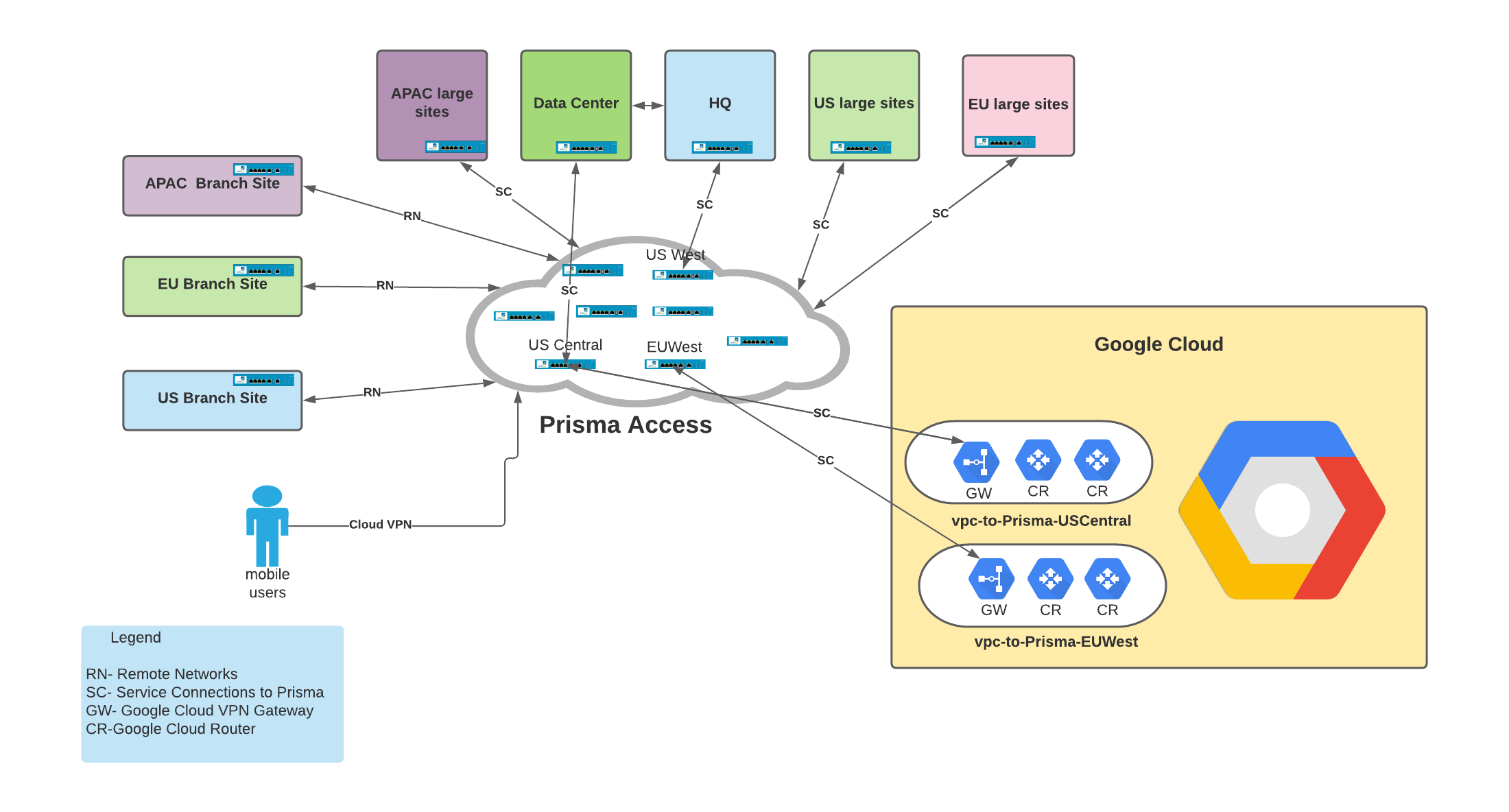
Prisma Access Resilience for Mobile Users
With a fully remote workforce, it’s critical that mobile users access IT Data Center and Google Cloud Platform (GCP) resources even if one of the GCP regions goes down. To achieve this, we made sure that service connections to IT Data Center, HQ and GCP are built from Prisma Access gateways in 2 different GCP regions as shown in figure 3. If a GCP region goes down, users can still access HQ/ Data Center and GCP.
What’s Next?
We hope you can use our approach in improving your security posture for intellectual property and mobile users.
Next up, we’re going to optimize connectivity, specifically for the following:
- Remote Networks: We’re working on converting all of our 20 branch IT sites to remote networks in Prisma Access.
- Converged WAN backbone for SD-WAN and Prisma Access: Our large sites and data centers connect through a SD-WAN mesh of Cloudgenix appliances, providing site-to-site application based routing capabilities in addition to all sites also connected through Prisma Access backbone, so remote users and sites in multiple geographical regions are securely connected.
I haven’t shown a picture for both SD-WAN backbones and Prisma Access backbones side-by-side on purpose because we’re looking to converge Prisma Access connectivity and SD-WAN connectivity over the same GCP backbone. We’d like to optimize the SD-WAN routing plane and the Prisma Access secure connectivity plane over the same backbone. Stay tuned for more on this next time!



